Steps for ECC
Step 1: The sender and receiver selects two integers 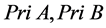 as private keys.
as private keys.
Step 2: The public keys of both sender and receiver are generated by multiplying the base point 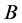 of the elliptic curve with the corresponding private keys.
of the elliptic curve with the corresponding private keys.
Public key of sender: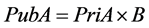 ;
;
Public key of receiver: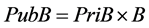 .
.
Step 3: The security key is generated as follows:
Secret Key of sender: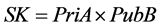 ;
;
Secret Key of receiver: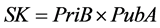 .
.
Step 4: The signature is generated using the hash functions.
Step 5: The signature is sent to the receiver for authentication.
Step 6: At the encryption phase, the message is converted into cipher text using the public keys and a point on the curve.
Step 7: The cipher text is decrypted at the receiver end using the private key.
Step 8: The signature is validated, if the sender’s public key is encoded in it.