Steps for key exchange
Step 1: Two integers such as a prime number 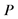 and a generator
and a generator 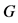 is selected by both the sender and the receiver.
is selected by both the sender and the receiver.
Step 2: Two random numbers 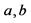 that are less than the prime number are selected as private keys.
that are less than the prime number are selected as private keys.
Step 3: The public keys of the sender and the receiver is computed as follows:
Public key of sender: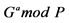 ;
;
Public key of receiver: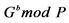 .
.
Step 4: These public keys were exchanged between the sender and the receiver via an insecure channel.
Step 5: The private keys are calculated as follows:
Private key of sender: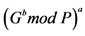 ;
;
Private key of receiver: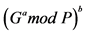 .
.
Step 6: Then, the shared secret key of both the sender and the receiver must be same i.e.,
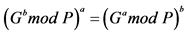 .
.