Steps for key generation
Step 1: Two dissimilar large prime numbers are selected in random.
Step 2: The key length of the public and private keys are represented in bits. The modulus of the keys are calculated as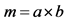 .
.
Step 3: The Euler’s function is calculated as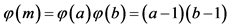 .
.
Step 4: An integer for public key, namely, 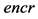 that lies between 1 and
that lies between 1 and 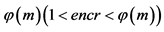 is selected, in such a way that
is selected, in such a way that 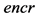 is a co-prime of
is a co-prime of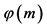 .
.
Step 5: The value of private key, namely, 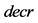 is computed as follows
is computed as follows 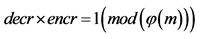 .
.
Step 6: The public that is used for encryption 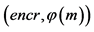 is published.
is published.
Step 7: The private key used for decryption  is kept safe along with the random prime numbers
is kept safe along with the random prime numbers 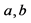 and the Euler’s function
and the Euler’s function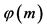 .
.