Protocol 1. Tag authentication protocol
SUMMARY: Authenticate the tag
1. Setup 1.1 The tag and the server share the common secret 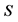 1.2 The reader gets the server’s public key
1.2 The reader gets the server’s public key 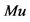 from the product manufacturer. 1.3 The reader gets the
from the product manufacturer. 1.3 The reader gets the  from the tag sticker. 1.4 The function
from the tag sticker. 1.4 The function  is a one-way function with three inputs:
is a one-way function with three inputs: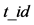 , random
, random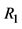 , and
, and .
.
2. Protocol messages. The protocol involves four messages The reader à the tag: 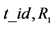 (1) The reader ß the tag:
(1) The reader ß the tag: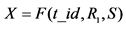 (2) The reader à the server:
(2) The reader à the server:  (3) The reader ß the server:
(3) The reader ß the server: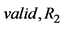 (4) The reader à the server:
(4) The reader à the server:  (5)
(5)
3. Protocol actions. The tag is authenticated as follows 3.1 The reader chooses a random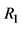 , and sends (1) to the tag. 3.2 If
, and sends (1) to the tag. 3.2 If 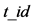 in (1) matches with the tag’s own
in (1) matches with the tag’s own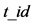 , the tag computes
, the tag computes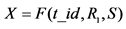 , and sends
, and sends  to the reader. Otherwise, the tag terminates the protocol. 3.3 The reader generates a random
to the reader. Otherwise, the tag terminates the protocol. 3.3 The reader generates a random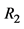 , encrypts
, encrypts 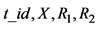 with
with , and sends (3) to the server. 3.4 The server decrypts (3) with its private key
, and sends (3) to the server. 3.4 The server decrypts (3) with its private key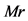 , and
, and
finds the tuple 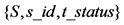 corresponding to . If
corresponding to . If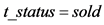 , the server sends (5) to the reader. Otherwise, the server computes
, the server sends (5) to the reader. Otherwise, the server computes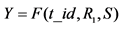 , and checks
, and checks . If so, the server sets
. If so, the server sets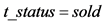 , and sends (4) to the reader. Otherwise, the server sends (5) to the reader. Finally, the server terminates the protocol.
, and sends (4) to the reader. Otherwise, the server sends (5) to the reader. Finally, the server terminates the protocol.